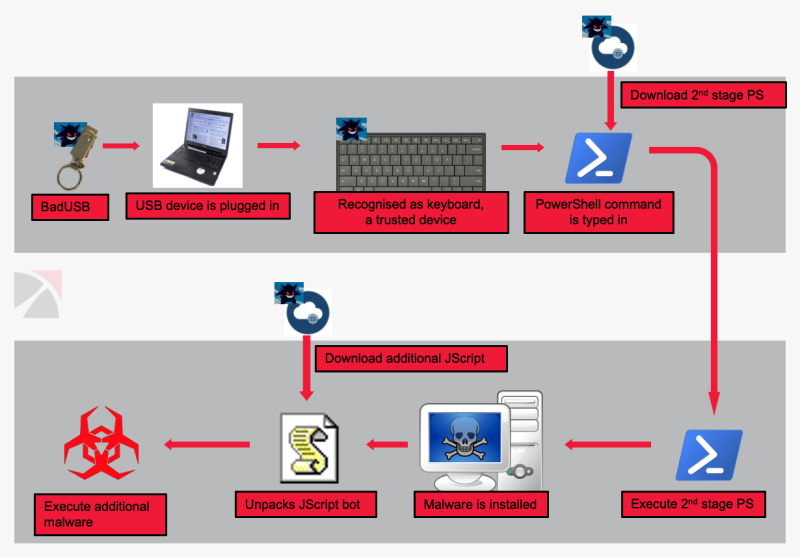
GitHub - B-U-K/Ducky-Credential-Harvester: Short credential harvester for the USB-Rubber-Ducky (Hak5). Requires the Twin-Duck firmware flashed on it.

Most Powerful BadUSB Payload on Flipper Zero! Keylogger w/ Credential Stealer & File Downloader! - YouTube
GitHub - GamehunterKaan/BadUSB-Browser: Steal All Browser Credentials Via BasUSB Attack In 5 Seconds.



/cdn.vox-cdn.com/uploads/chorus_asset/file/23949203/226141_rubberDucky.jpg)