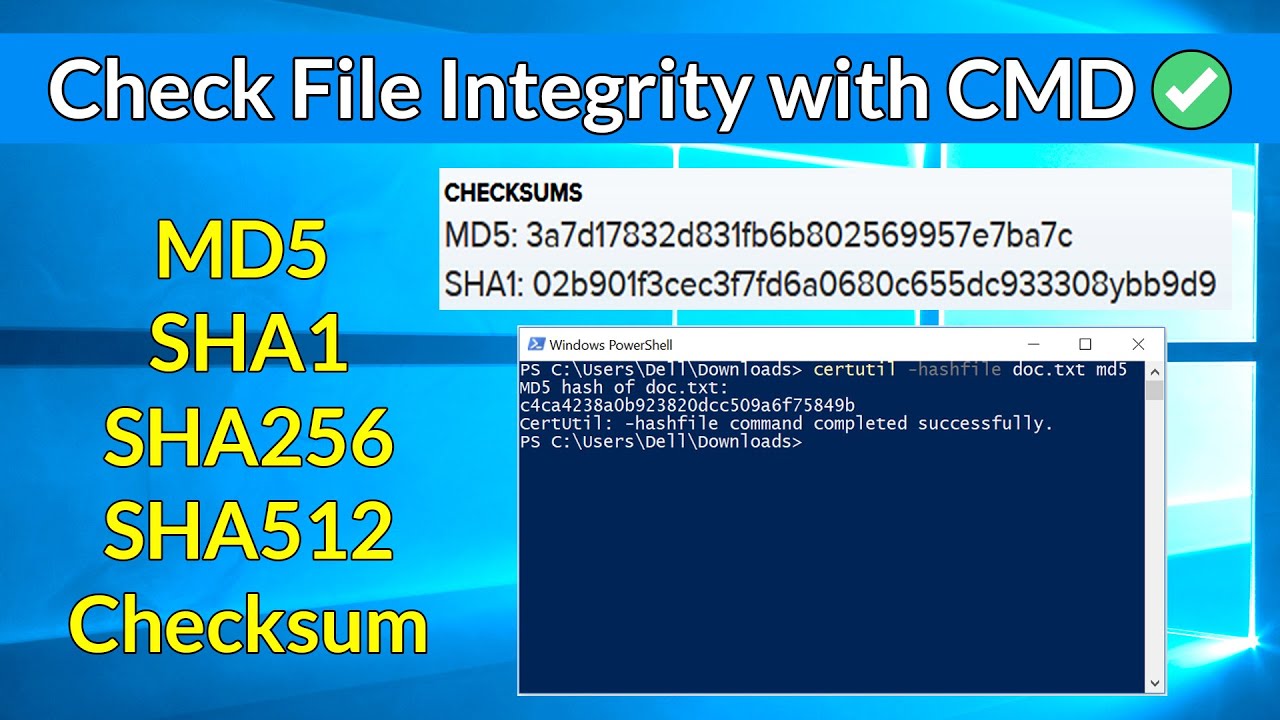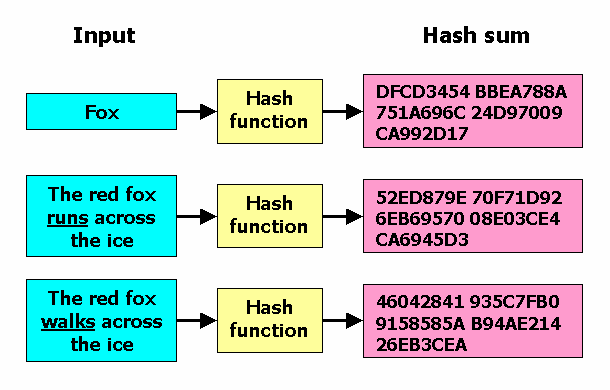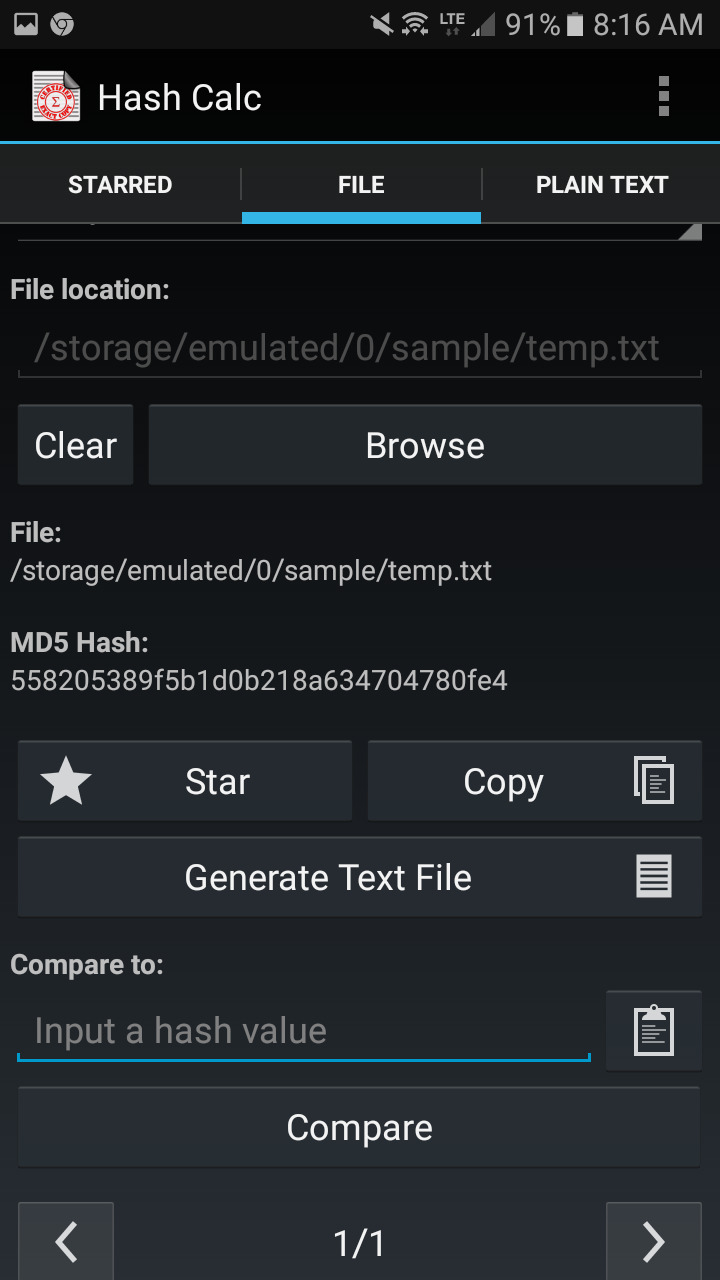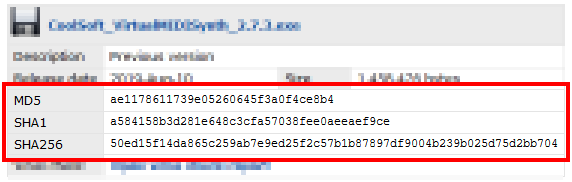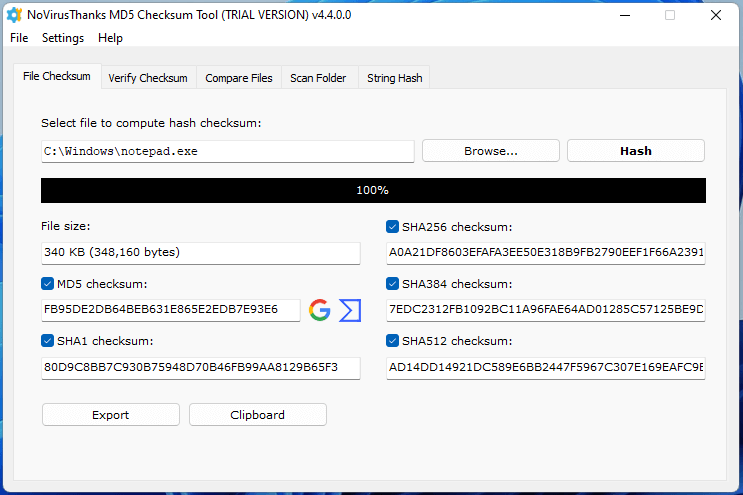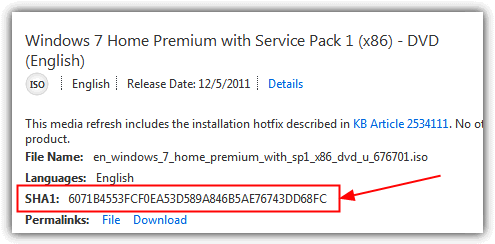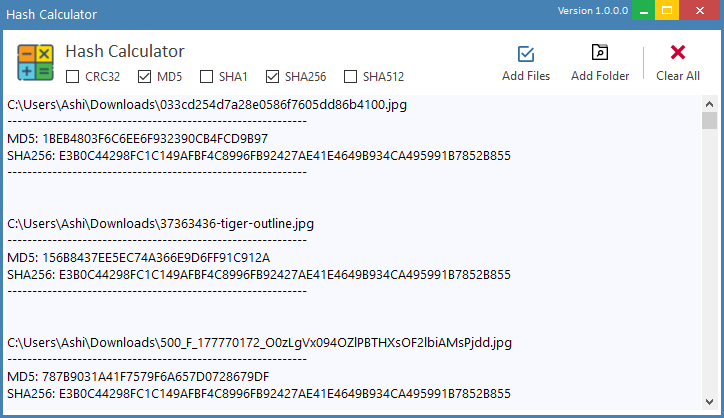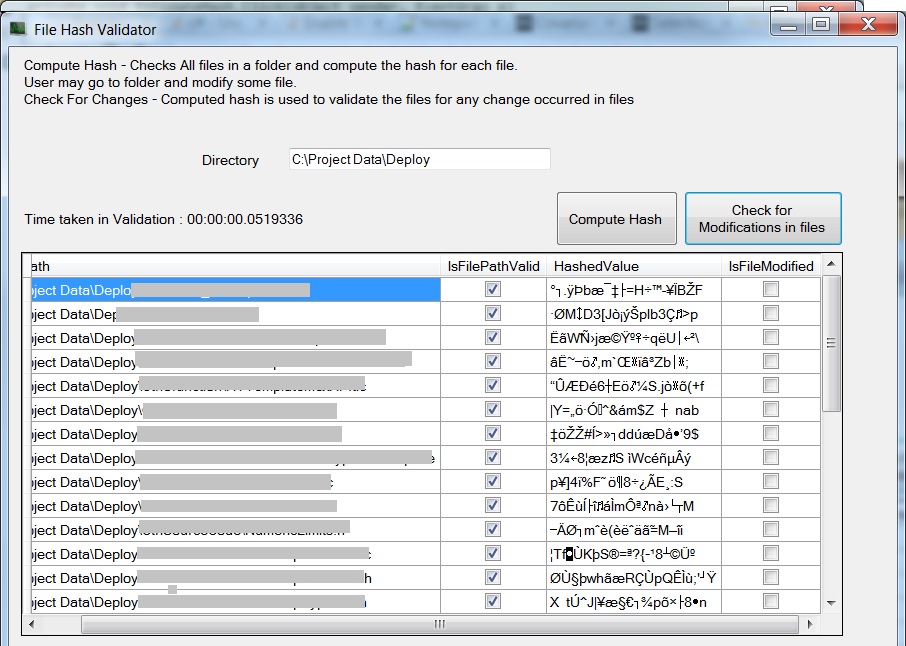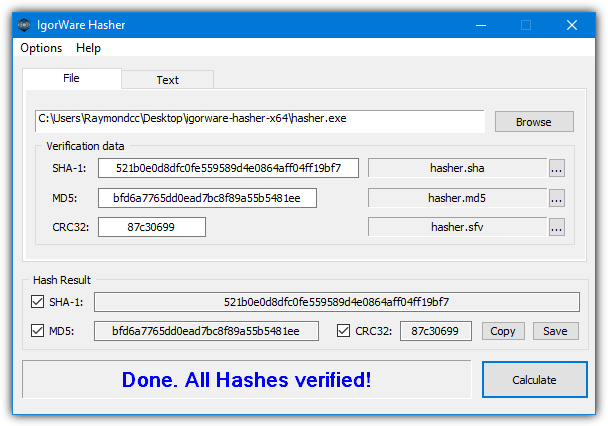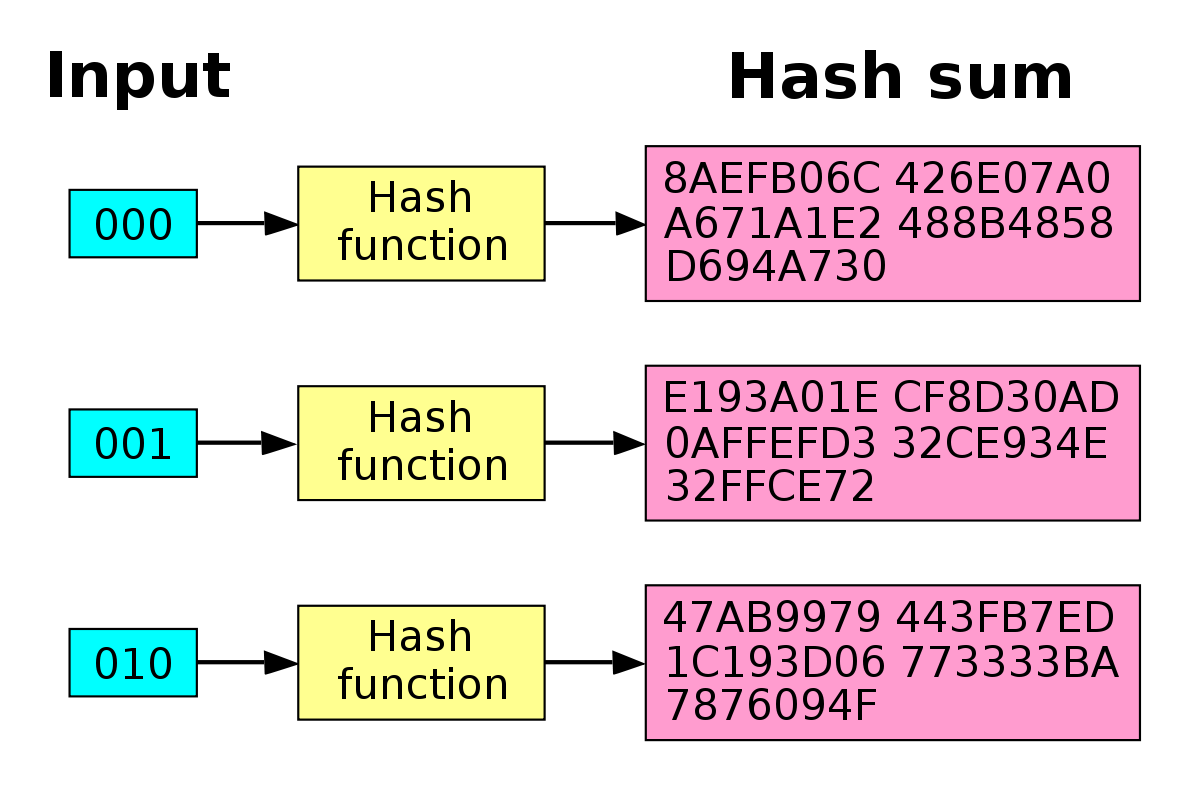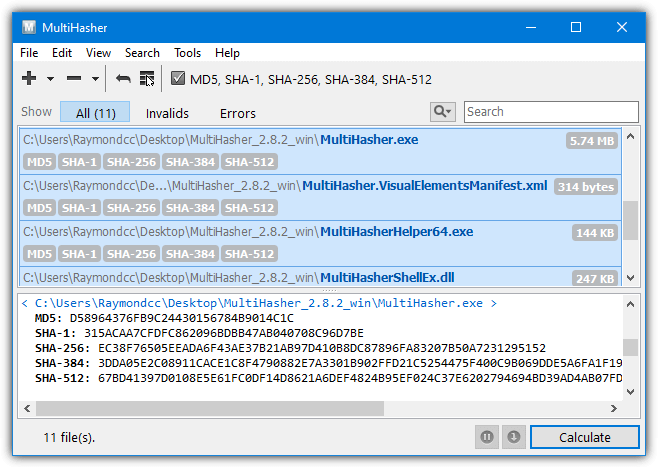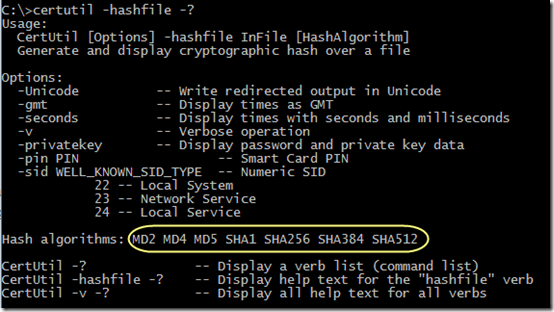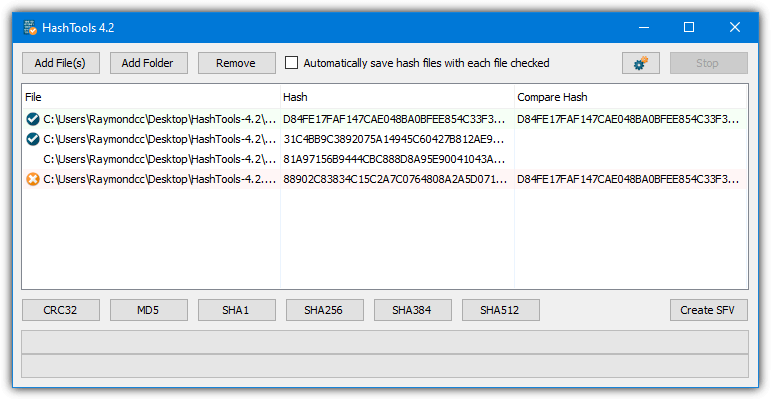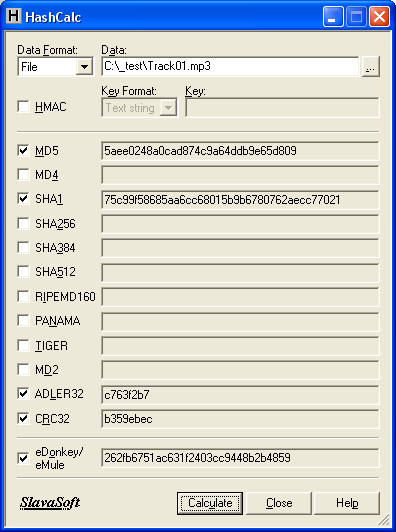
Hash Calculator to Get, Compute and Calculate MD5 and SHA1 File Checksum or Hash Value - Tech Journey

Computer Forensics, Malware Analysis & Digital Investigations: EnCase v7 EnScript to quickly provide MD5/SHA1 hash values and entropy of selected files