Computer Security and PGP: What Is Diffie - Hellman Key Exchange Protocol or Oakley Protocol? | Computer security, Secret, Security

Components of IPSEC - CCIE IP SEC - Main Components of IP SEC - IKE, ESP and AH - Networkers Home - YouTube

Oakley Wind Jacket - Tom Cruise - Mission: Impossible – Ghost Protocol | Sunglasses ID - celebrity sunglasses

COVID-19_arXiv on Twitter: "𝗧𝗶𝘁𝗹𝗲: Protocol for a Sequential, Prospective Meta-Analysis to Describe COVID-19 in Pregnancy and Newborn Periods. 𝗔𝘂𝘁𝗵𝗼𝗿𝘀: Emily R. Smith, Siran He, Erin M Oakley, Lior Miller, James M Tielsch

IPSec Key Management|Oakley Key|ISAKMP Protocol|Lecture-02|Bca 6th Sem|By Sarvesh Sir|IICS College - YouTube


![PDF] A Survey on IPSEC Key Management Protocols | Semantic Scholar PDF] A Survey on IPSEC Key Management Protocols | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3aaf2b37a95d94412046ef3b9cdc4d3439b750b2/4-Figure1-1.png)
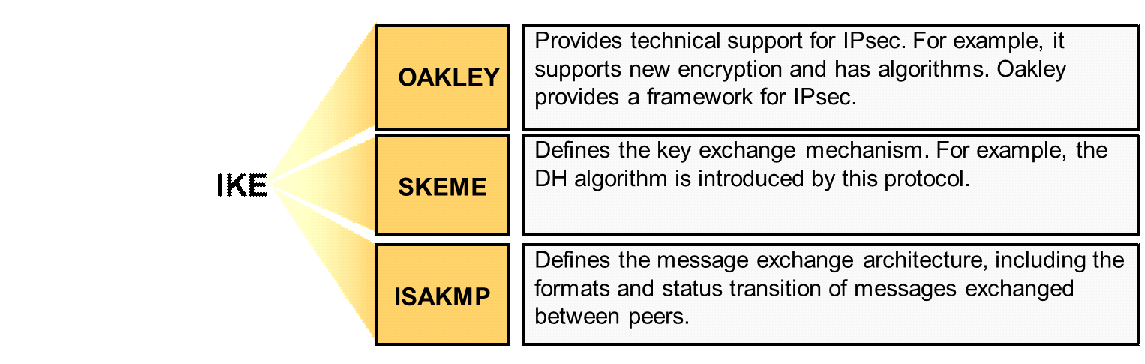





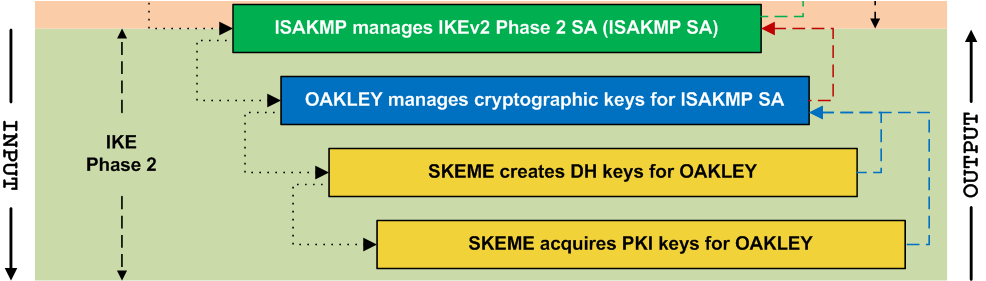
![Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram](https://www.researchgate.net/publication/297336095/figure/fig4/AS:558684922224640@1510212273285/Operation-of-SA-other-protocols-OAKLEY-SKEME-and-ISAKMP-8-5-OAKLEY-it-is-a-key.png)

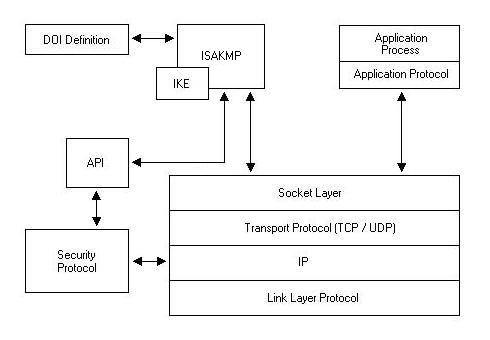





![Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram Operation of SA other protocols: OAKLEY, SKEME and ISAKMP [8] [5].... | Download Scientific Diagram](https://www.researchgate.net/profile/Riaz-Khan-19/publication/341151254/figure/fig4/AS:887753323581444@1588668294660/Operation-of-SA-other-protocols-OAKLEY-SKEME-and-ISAKMP-8-5-OAKLEY-it-is-a-key_Q640.jpg)