Amazon.com: USB Defender | Data Blocker | Blocks Unwanted Data Transfers | Protects Smartphone & Tablets From Public Charging Stations | Hack Proof, 100% Guaranteed : Electronics

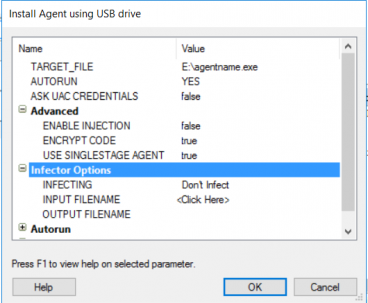
How I made a programmable hacking USB device to infiltrate PCs? | by Aditya Anand | InfoSec Write-ups

Tip! If you find yourself plugging in the exploit usb alot, get yourself a usb with a switch. : r/ps4homebrew

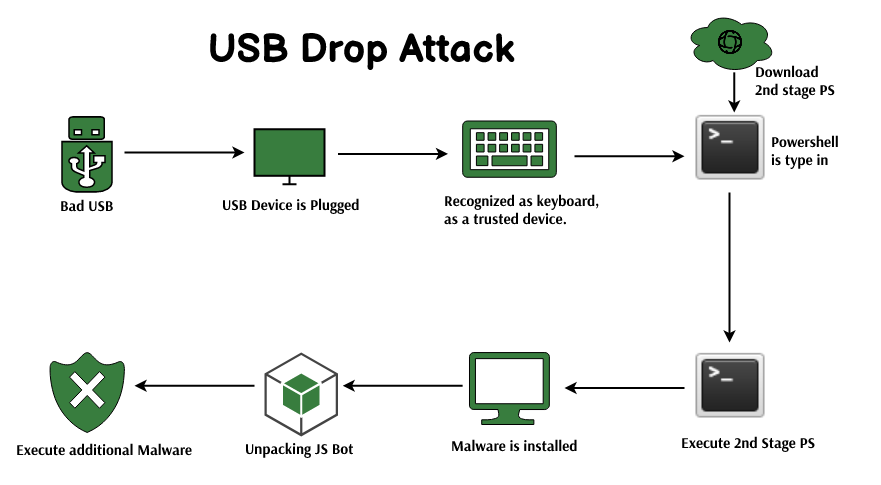
USB Device Under Threat. New Hack Is Undetectable And Unfixable – Cyber Security Experts – Middle East | Eastern Province | Al-Khobar, Kingdom of Saudi Arabia